上一年(2022年)10月份左右开始,谷歌翻译退出中国大陆,导致中国大陆地区的chrome自带翻译无法使用。目前网上的解决方案主要是修改hosts或者挂系统代理,但这两种方法一个容易失效,另一个不够方便,因此本文将向你介绍一种不一样的解决方法。
写在前面
如果你不想折腾,你可以直接下载这个压缩包,按照README里的教程操作即可,开箱即用。
如果上面的下载地址失效了可以用这个备用下载地址
因为workers每日调用额度只有10万次,如果太多人用,我自建的服务端可能会超限然后无法使用,所以强烈推荐大家自建服务端
如果你感兴趣的话可以继续往下看(●’◡’●)
原理说明
本文介绍的方法是:「两层反向代理」,即先用cloudflare或者vercel反代谷歌翻译的api translate.googleapis.com ,再在本地用nginx反代第一层反代的域名
哈吉马路哟!
下面开始正式教程
配置服务端反代(配置服务端)
首先我们要用cf或者vercel反代谷歌翻译的api
cloudflare
如果你选择使用cf的话,请参考以下步骤
1.打开cloudflare面板,进入“workers”页面
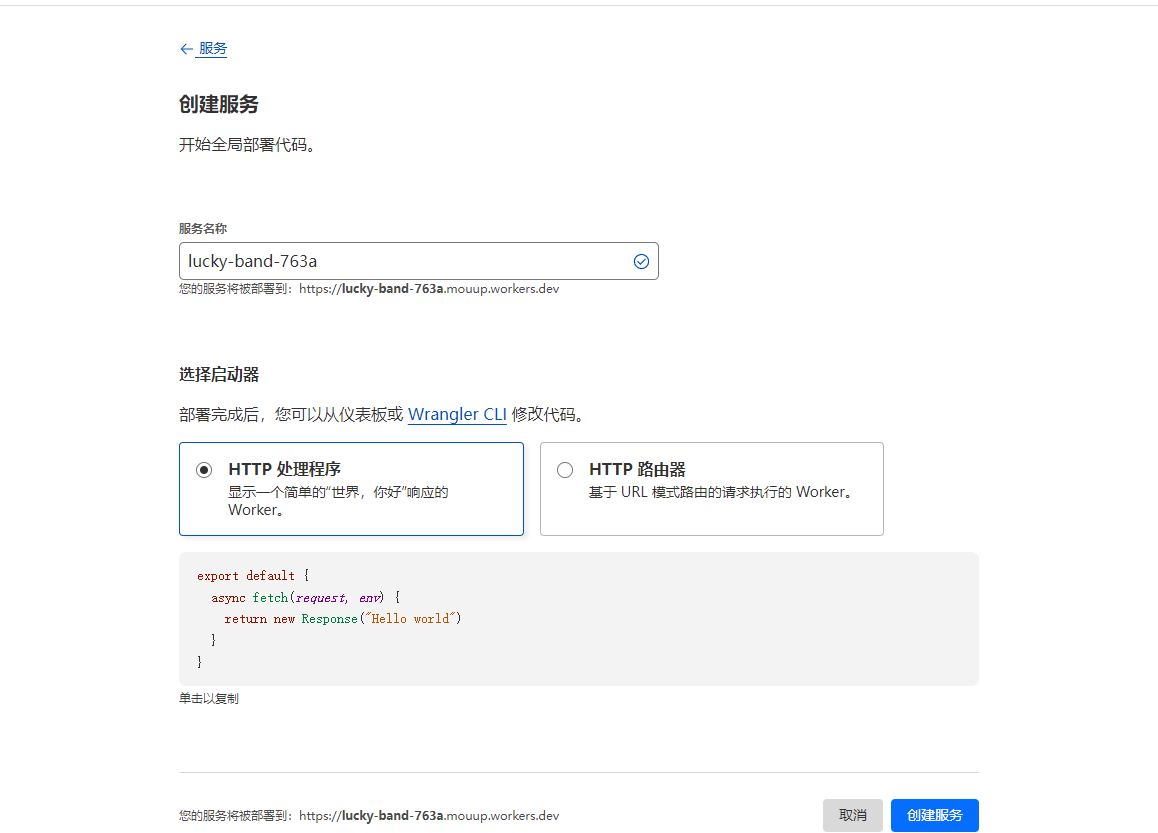
点击创建服务
点击快速编辑,替换为以下内容
const hostname = "https://translate.googleapis.com"
function handleRequest(request) {
let url = new URL(request.url);
return fetch(new Request(hostname + url.pathname,request))
}
addEventListener("fetch", event => {
event.respondWith(handleRequest(event.request))
})
点击保存部署
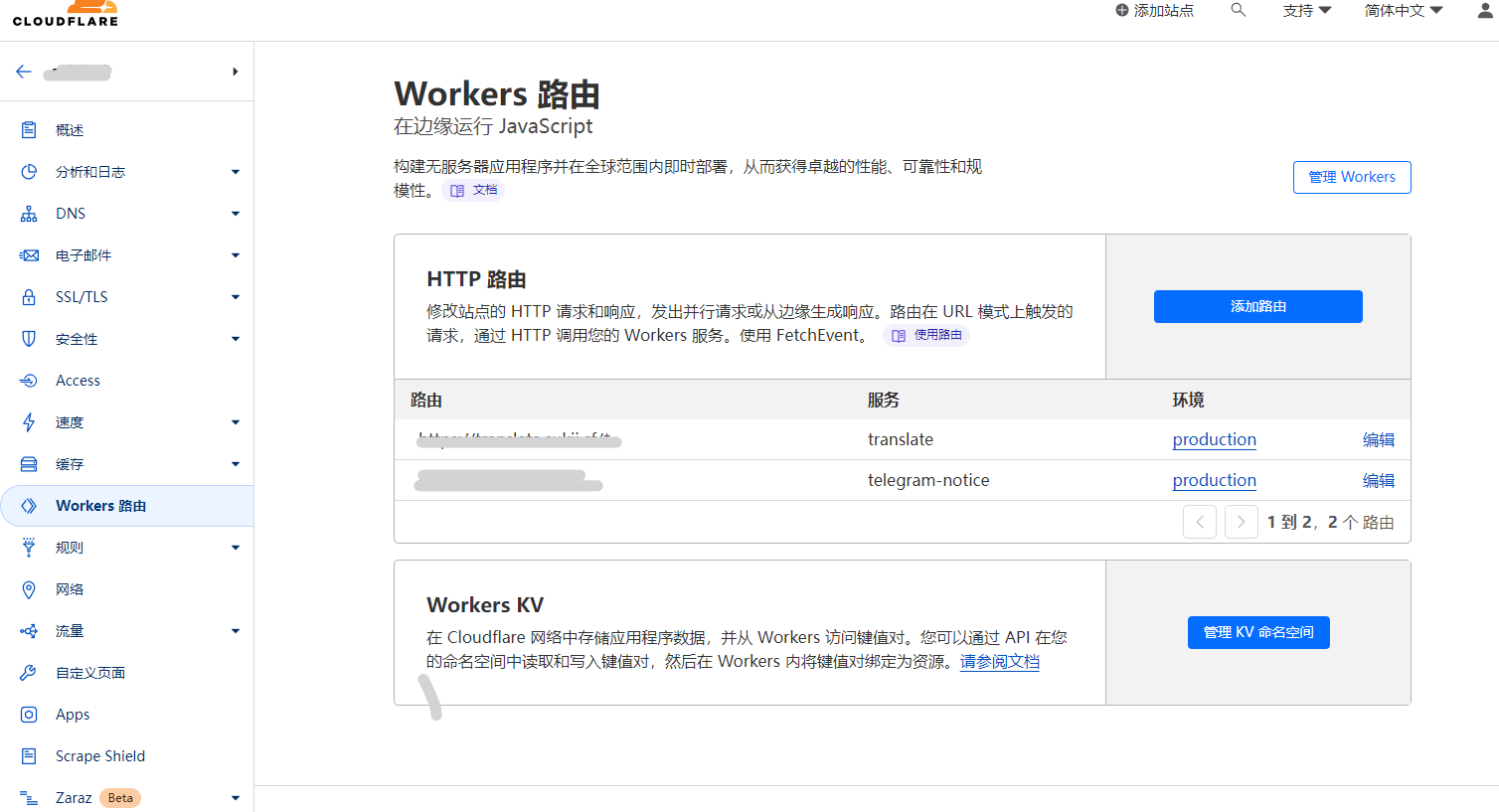
2.设置workers路由
因为workers.dev被墙了
回到主页,点击“网站”
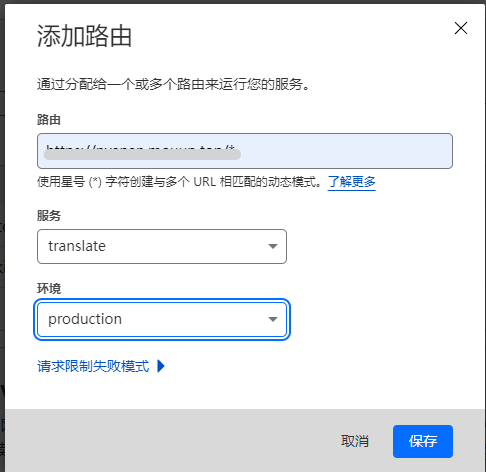
点进你的域名,新建一条A记录,名称随意(这里我用translate),ip地址随便填(比如我填8.8.8.8),一定要把云朵点上!
“路由”填https://<你前面弄的域名>/*
“服务”选择之前的那个workers
“环境”为production
保存即可
如果设置正确,大概一两分钟后,访问你设置的域名就可以肯定这样的页面了
(别被404吓到了,这是正常的。另外,一般情况下谷歌的图标是显示不出来的)
vercel
如果你不想用cf而是选择用vercel,你可以参考以下内容进行配置
首先注册vercel账号
然后用以下命令在本地安装vercel cli(注意,你必须先安装node)
npm i -g vercel
然后登录vercel
vercel login
随便找个文件夹新建一个json文件,名字随意,粘贴以下内容
{
"version": 2,
"routes": [
{"src": "/(.*)","dest": "https://translate.googleapis.com/$1"}
]
}
保存退出,在json文件所在目录呼出终端,运行以下命令
verceL-A <文件名>.json--prod
按步骤部署,一般一直回车就行了
部署完成后打开vercel的面板,为这个project绑定一个域名,这里不多赘述
因为vercel.app也被污染了
到这里我们就完成了服务端的部署
本地反代
下载nginx
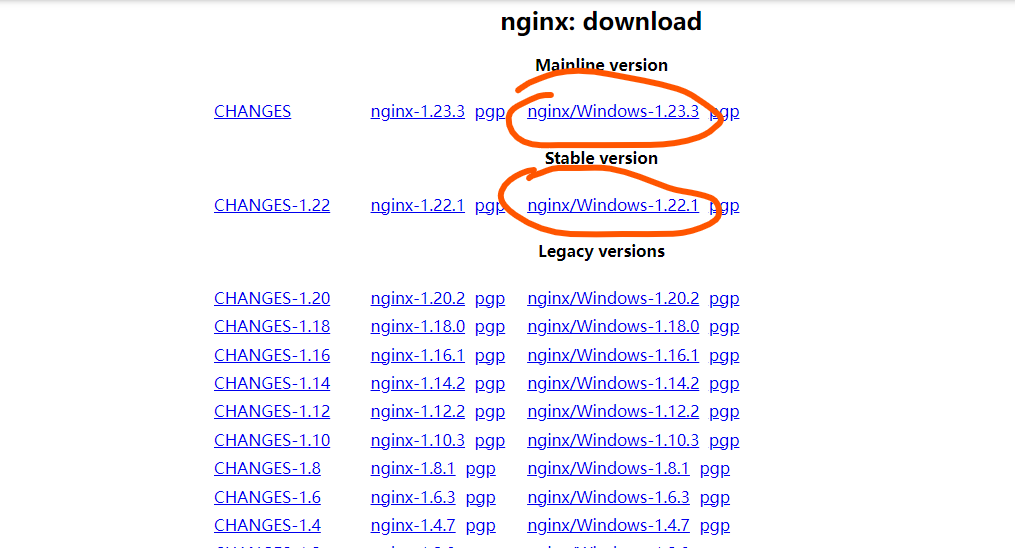
首先下载nginx
一般下载稳定版就好了
自签证书
0.你首先需要安装好openssl
1.创建CA证书
创建CA证书
openssl genrsa -out nyaCA.key 2048
生成CA公钥
openssl req -new -x509 -key nyaCA.key -out nyaCA.cer -days 36500
按说明输入信息,其中Common可以随便填
2.创建服务器证书
首先生成服务器秘钥
openssl genrsa -out server.key 2048
创建签名请求
新建一个名叫openssl.cnf的文件,粘贴以下内容
tsa_policy2 = 1.2.3.4.5.6
tsa_policy3 = 1.2.3.4.5.7
[ ca ]
default_ca = CA_default # The default ca section
[ CA_default ]
dir = ./demoCA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number file
x509_extensions = usr_cert # The extentions to add to the cert
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = default # use public key default MD
preserve = no # keep passed DN ordering
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 1024
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extentions to add to the self signed cert
string_mask = utf8only
req_extensions = v3_req # The extensions to add to a certificate request
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Mama
localityName = Locality Name (eg, city)
0.organizationName = Organization Name (eg, company)
0.organizationName_default = nya
organizationalUnitName = Organizational Unit Name (eg, section)
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 4
challengePassword_max = 20
unstructuredName = An optional company name
[ usr_cert ]
basicConstraints=CA:FALSE
nsCertType = client, email, objsign
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
[ svr_cert ]
basicConstraints=CA:FALSE
nsCertType = server
keyUsage = nonRepudiation, digitalSignature, keyEncipherment, dataEncipherment, keyAgreement
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
extendedKeyUsage = serverAuth,clientAuth
[ v3_req ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = translate.googleapis.com
[ v3_ca ]
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = CA:true
[ crl_ext ]
authorityKeyIdentifier=keyid:always
[ proxy_cert_ext ]
basicConstraints=CA:FALSE
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
proxyCertInfo=critical,language:id-ppl-anyLanguage,pathlen:3,policy:foo
[ tsa ]
default_tsa = tsa_config1 # the default TSA section
[ tsa_config1 ]
dir = ./demoCA # TSA root directory
serial = $dir/tsaserial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/tsacert.pem # The TSA signing certificate
# (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply
# (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
default_policy = tsa_policy1 # Policy if request did not specify it
# (optional)
other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional)
digests = md5, sha1 # Acceptable message digests (mandatory)
accuracy = secs:1, millisecs:500, microsecs:100 # (optional)
clock_precision_digits = 0 # number of digits after dot. (optional)
ordering = yes # Is ordering defined for timestamps?
# (optional, default: no)
tsa_name = yes # Must the TSA name be included in the reply?
# (optional, default: no)
ess_cert_id_chain = no # Must the ESS cert id chain be included?
# (optional, default: no)
保存后运行以下命令
openssl req -config openssl.cnf -new -out server.req -key server.key
注意这里的Common Name填translate.googleapis.com
通过CA机构证书对服务器证书进行签名
openssl x509 -req -extfile openssl.cnf -extensions v3_req -in server.req -out server.cer -CAkey nyaCA.key -CA nyaCA.cer -days 36500 -CAcreateserial -CAserial serial
然后将生成的server.cer(公钥)和server.key(密钥)部署到nginx
3.信任CA机构证书
如果是Windows的话直接双击生成的nyaCA.cer,将证书导入到受信任的根证书颁发机构即可
自签证书部分参考了这篇文章
如果你懒得折腾可以直接用我给你的压缩包里签好的证书
修改nginx配置文件
修改conf目录下的nginx.conf文件
在http的大括号内加入include tranlate.conf;(不要漏了分号)
在conf目录下新建一个名叫translate.conf的文件,粘贴以下内容
server {
listen 443 ssl;
server_name translate.googleapis.com;
ssl_certificate <公钥路径>;
ssl_certificate_key <私钥路径>;
client_max_body_size 50M;
location /
{
proxy_pass https://<服务端域名>; #注意后面没有“/”
proxy_set_header Host <服务端域名>;
#向后端传递访客 ip
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header REMOTE-HOST $remote_addr;
#向后端传递访客 ip (反代CF增加规则)
proxy_ssl_name <服务端域名>;
proxy_ssl_server_name on;
}
}
修改其中的<服务端域名>、<公钥路径>、<私钥路径>
运行nginx
建议先在nginx.exe所在目录用终端运行nginx,看看有没有报错
如果一切正常就可以双击nginx.exe让nginx在后台运行了
修改hosts
在C:\Windows\System32\drivers\etc下的hosts文件中添加
127.0.0.1 translate.googleapis.com
开机自启
为nginx.exe创建快捷方式,然后将快捷方式复制到目录C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp下即可
至此大功告成